Firewall Network Security - Cisco ASA 5500 Series SSL/IPsec VPN Edition
The Cisco® ASA 5500 Series Adaptive Security Appliance is a purpose-built platform that combines best-in-class security and VPN services for small and medium-sized business (SMB) and enterprise applications. The Cisco ASA 5500 Series enables customization for specific deployment environments and options, with special product editions for SSL/IPsec VPN, Firewall Network Security, Content Security, and Intrusion Prevention.
The Cisco ASA 5500 Series SSL/IPsec VPN Edition enables organizations to gain the connectivity and cost benefits of Internet transport without compromising the integrity of corporate security policies. By converging Secure Sockets Layer (SSL) and an IP Security (IPsec) VPN service with comprehensive threat defense technologies, the Cisco VPN client delivers highly customizable network access tailored to the requirements of diverse deployment environments while providing advanced endpoint and network-level security (Figure 1).
Figure 1. A Customizable VPN Service for any Deployment Scenario
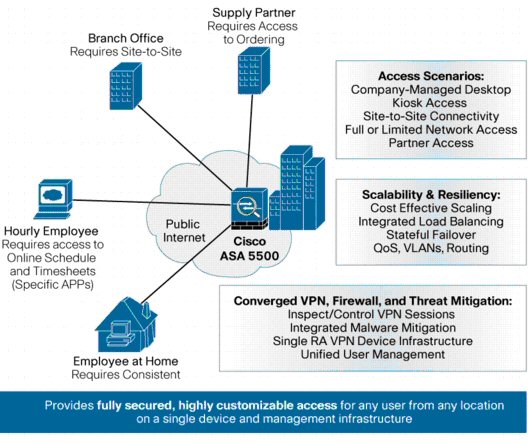
Cisco ASA 5500 Series SSL/IPSEC VPN Edition
The Cisco ASA 5500 Series SSL/IPsec VPN Edition offers flexible VPN technologies for any connectivity scenario, with scalability up to 5000 concurrent users per device. It provides easy-to-manage, full-tunnel network access through SSL, Datagram Transport Layer Security (DTLS), IPsec VPN client technologies, advanced clientless SSL VPN capabilities, and network-aware site-to-site VPN connectivity, enabling secure connections across public networks to mobile users, remote sites, contractors, and business partners. Costs associated with VPN deployment and operations are reduced by eliminating ancillary equipment required to scale and secure a VPN.
Benefits of the Cisco ASA 5500 Series SSL/IPsec VPN Edition include:
Network Remote Access
Full network access provides network-layer remote-user connectivity to virtually any application or network resource and is often used to extend access to managed computers such as company-owned laptops. Connectivity is available through the automatically downloaded Cisco AnyConnect VPN Client, the Cisco IPsec VPN Client, and the Microsoft and Mac OS X Layer 2 Tunneling Protocol (L2TP)/IPsec VPN clients. The Cisco AnyConnect VPN Client will automatically adapt its tunneling protocol to the most efficient method based on network constraints and is the first VPN product to use the DTLS protocol to provide an optimized connection for latency-sensitive traffic, such as voice over IP (VoIP) traffic or TCP-based application access. By supporting SSL, DTLS, and IPsec-based remote-access VPN technologies, the Cisco ASA 5500 Series delivers unsurpassed flexibility to meet the needs of the most diverse deployment scenarios.
Remote-User Connectivity
Full network access provides network-layer remote-user connectivity to virtually any application or network resource and is often used to extend access to managed computers such as company-owned laptops. Connectivity is available through the automatically downloaded Cisco AnyConnect VPN Client, the Cisco IPsec VPN Client, and the Microsoft and Mac OS X Layer 2 Tunneling Protocol (L2TP)/IPsec VPN clients. The Cisco AnyConnect VPN Client will automatically adapt its tunneling protocol to the most efficient method based on network constraints and is the first VPN product to use the DTLS protocol to provide an optimized connection for latency-sensitive traffic, such as voice over IP (VoIP) traffic or TCP-based application access. By supporting SSL, DTLS, and IPsec-based remote-access VPN technologies, the Cisco ASA 5500 Series delivers unsurpassed flexibility to meet the needs of the most diverse deployment scenarios.
Clientless Remote Access
Clientless remote access provides access to network applications and resources, regardless of location, without the need for desktop VPN client software. Using the ubiquity of SSL encryption available in Internet browsers, the Cisco ASA 5500 Series delivers clientless access to any Web-based application or resource, terminal services applications such as Citrix, and optimized Microsoft Outlook Web access and Lotus iNotes, as well as access to common thick-client applications like e-mail and calendering, instant messaging, FTP, Telnet, and SSH. Additionally, the superior content rewriting capabilities of the Cisco ASA 5500 Series help ensure reliable rendering of complex Web pages with Java, JavaScript, ActiveX, Flash, and other sophisticated content.
High-Speed Internet via VPN
Secure, high-speed internet communications are possible between multiple office locations. Support for quality of service (QoS) and routing across the VPN helps ensure reliable, business-quality delivery of latency-sensitive applications like voice, video, and terminal services.
VPN Security: Cisco ASA 5500
VPNs are a primary source of malware infiltration into networks. Malware includes worms, viruses, spyware, keyloggers, Trojan horses, and rootkits. The depth and breadth of intrusion prevention, antivirus, application-aware firewall, and VPN security capabilities in the Cisco ASA 5500 Series minimizes the risk that the VPN connection will become a conduit for security threats.
Cost-effective VPN - VPN Products
Scaling and securing VPNs often requires additional load balancing and security equipment, which increases both equipment and operational costs. The Cisco ASA 5500 Series integrates these functions, delivering an unprecedented level of network and security integration among the VPN products available today. And by offering support for flexible tunneling options on a single platform, the Cisco ASA 5500 Series provides customers with cost-effective VPN alternatives to deploying parallel VPN infrastructures.
Scalability and resiliency
The Cisco ASA 5500 Series can support up to 5000 simultaneous user sessions per device, with the ability to scale to tens of thousands of simultaneous user sessions through integrated clustering and load-balancing capabilities. Stateful failover features deliver high-availability services for unsurpassed uptime.
Customizable Remote-Access VPN Features
Find out more about the Cisco VPN client remote-access features by clicking on the links in the table below:
| Feature | Included | |||||
|---|---|---|---|---|---|---|
|
||||||
Optimised Network Access
|
 |
|||||
Operating System CompatibilityOperating system compatibility and OS support is available on Cisco for the following systems:
|
 |
|||||
Installing Cisco: DeploymentCisco: Deployment options:
Connection modes:
|
 |
|||||
Cisco AnyConnect: VPN ClientThe Cisco AnyConnect VPN Client allows an administrator to automatically distribute software and policy updates from the headend security appliance, thereby eliminating administration associated with VPN client software updates |
 |
|||||
VPN Client: Consistent User Experience
|
 |
|||||
Advanced IP Network Connectivity
IP address assignment mechanisms:
|
 |
|||||
| ||||||
Programming Language CompatibilityThe Cisco advanced transformation capability helps ensure programming language compatibility with web pages containing complex content and programming languages, including; HTML, Java, ActiveX, JavaScript, and Flash. |
 |
|||||
Clientless VPN & Integrated OptimisationCisco is a clientless VPN with integrated optimisation for resource-intensive applications, such as Microsoft Outlook Web Access and Lotus iNotes, delivers exceptional response times and low latency to provide a high-quality SSL VPN end-user experience. |
 |
|||||
Cisco Clientless PortalThe enhanced Cisco clientless portal features group-based customization features for detailed access, ease of use, and a customizable user experience:
|
 |
|||||
Clientless SSL VPN: Citrix AccessNo extraneous helper applications are required for Citrix access over clientless SSL VPN, which helps ensure fast application initiation time and reduces the risk of desktop software conflicts. |
 |
|||||
Integrated ClientCisco provides integrated client and server application support via access to common client/server applications without the need for pre-deployed remote clients, granting rapid access to Telnet, SSH, Remote Desktop Protocol (RDP), and Virtual Network Computing (VNC) resources. |
 |
|||||
Email Port ForwardingEmail port forwarding enables clientless access to popular thick client applications like Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), e-mail, online calendars, instant messaging, Telnet, SSH, and other client-initiated TCP applications via a small Java applet. Smart tunneling allows Microsoft Windows users access to TCP applications without the prerequisite of administrative rights and allows VPN administrators to grant only approved applications access to internal resources. |
 |
|||||
Browser CompatibilityCisco cross browser support, includes browser compatibility with Microsoft Internet Explorer, Firefox, Opera, Safari, and Pocket Internet Explorer (PIE) to ensure broad connection compatibility from any location. |
 |
|||||
Advanced IP NetworksAccess to internal IPv4 and IPv6 network resources. |
 |
|||||
|
||||||
Cisco Authentication Options
|
 |
|||||
Intelligent Services GatewayCisco Intelligent Services Gateway provides sophisticated authorisation capabilities:
|
 |
|||||
Clientless SSL VPN - Single Sign On (SSO)Technical details for Clientless SSL VPN with single sign on (SSO):
|
 |
|||||
Threat-Protected VPN Service
The Cisco ASA 5500 Series SSL/IPsec VPN Edition provides advanced security for VPN deployments through its integrated network and endpoint security technologies. Securing the VPN is necessary to ensure it prevents network attacks such as worms, viruses, spyware, keyloggers, Trojan horses, rootkits, or hacking. Detailed application and access control policy helps ensure that individuals and groups of users have access only to the applications and network services to which they are entitled (Figure 2).
Figure 2. Threat-Protected VPN Services Use Onboard Security to Protect Against VPN Threats
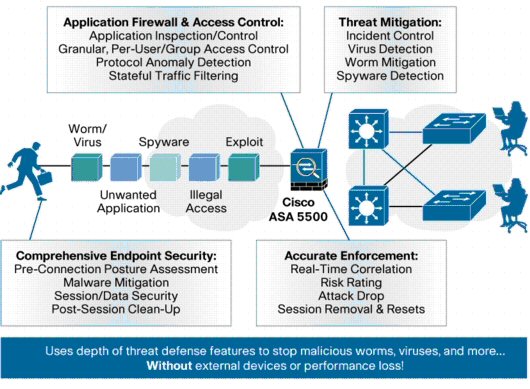
Network Security at the VPN Gateway
Worms, viruses, application-embedded attacks, and application abuse are among the greatest security challenges in today's networks. Remote access and remote-office VPN connectivity are common points of entry for such threats due to limited security capabilities on VPN devices. VPNs are often deployed without proper inspection and threat mitigation applied at the tunnel termination point at the headquarters location, which allows malware from remote offices or users to infiltrate the network and spread. With the converged threat mitigation capabilities of the Cisco ASA 5500 Series, customers can detect malware and stop it before it enters the network interior. For application-embedded attacks, such as spyware or adware spread through file-sharing peer-to-peer networks, the Cisco ASA 5500 Series deeply examines application traffic to identify a dangerous payload and drops its contents before it reaches its target and causes damage. The table below lists some VPN gateway security features provided by the Cisco VPN Client.
| Feature | Included | ||
|---|---|---|---|
|
|||
Malware Mitigation and Virus ProtectionCisco antivirus provides extensive malware mitigation and virus protection against worms, viruses, spyware, keyloggers, Trojan horses, and rootkits. The Cisco ASA 5500 Series VPN gateway is a secure solution that eliminates threats before they spread throughout the network. |
 |
||
Application-Aware Firewall and Access ControlCisco systems application-aware firewall provides traffic inspection that enables thorough user access control and helps prevent abuse of unwanted applications, such as peer-to-peer file sharing across the VPN connection. |
 |
||
Intrusion Prevention SystemThe Cisco ASA 5500 Series intrusion prevention system guards against a multitude of network exploits. |
 |
||
Cisco Access RestrictionsCisco access restrictions provide permission or denial of access to confidential resources is based on flexible configuration policies and current posture status. |
 |
||
Virtual LAN Mapping (VLAN Mapping)Information about the CCS Leeds virtual LAN mapping (VLAN mapping) service: Enforcement of user and group-based traffic access restrictions are based on a configured VLAN. |
 |
||
|
|||
Pre-Connection Posture AssessmentThe Host integrity verification checking on Cisco systems seeks to detect the presence of antivirus software, personal firewall software, and Windows service packs on the endpoint system prior to granting network access. A significantly expanded list of applications and versions are now supported through this mechanism. Frequent updates are available to support new product releases. Administrators also have the option of defining custom posture checks based on the presence of running processes. |
 |
||
Secure Desktop and Watermark CheckingCisco Secure Desktop can detect the presence of a watermark on a remote system. The watermark can be used to identify assets that are corporate-owned and provide differentiated access as a result. The watermark checking capability includes system registry values, file existence matching a required CRC32 checksum, IP address range matching, and certificate issued by/to matching. |
 |
||
Data Protection: Cisco SecurityAdditional protection is provided for all data associated with the session, including passwords, file downloads, history, cookies, and cache files. Session data is encrypted to the secure vault of Cisco Secure Desktop. |
 |
||
Data Cleansing and Data CleanupData in the secure vault experiences data cleansing and is overwritten with the Cisco data cleanup functionality at the end of the session. |
 |
||
Keylogger DetectorCisco Secure Desktop includes a keylogger detector tool that performs an initial check for certain software-based keystroke logging software at the start of the session. The keystroke logger detection tool will flag up if an anomalous program begins running inside the secure vault, after session initiation, the user is prompted to stop the suspicious activity. |
 |
||
Cisco Permissions: Guest AccountsUsers accessing the network from remote machines may not have administrator privileges on all systems with Cisco permissions. Cisco Secure Desktop can often be installed with only guest accounts. This helps to ensure delivery and installation on all systems for multiple users. |
 |
||
Advanced Endpoint AssessmentAn advanced endpoint assessment option is available to automate the process of repairing out-of-compliance applications. |
 |
||
|
|||
QoS-EnabledSupports latency-sensitive applications like voice, video, and terminal services. |
 |
||
Network Integration and RoutingOpen Shortest Path First (OSPF) support across tunneling neighbors enables network topology awareness for ease of network integration. |
 |
||
|
|||
Network Security: Endpoint SecurityCisco network security and endpoint security provides onboard malware mitigation, IPS, and firewall capabilities increasing VPN security while decreasing the amount of equipment that needs to be deployed. |
 |
||
Load Balancing: Cisco SystemsCisco systems integrated load balancing features enable multichassis clusters without expensive external load balancing equipment. |
 |
||
Firewall Network Security: Cisco ASA 5500 Series Platform Overview
The Cisco ASA 5500 Series delivers site-specific scalability, from small offices to enterprise headquarter locations, through its five models: 5505, 5510, 5520, 5540, and 5550 (Figure 3). Models 5510 and up share a common chassis, built with a foundation of concurrent services scalability, investment protection, and future technology extensibility. The table below lists the specifications of the Cisco ASA 5500 Series models.
Figure 3. The Cisco ASA 5500 Series

Specifications of Cisco ASA 5500 Series Adaptive Security Appliances:
| Platform | Cisco ASA 5505 | Cisco ASA 5510 | Cisco ASA 5520 | Cisco ASA 5540 | Cisco ASA 5550 | |
|---|---|---|---|---|---|---|
| Maximum VPN Throughput | 100 Mbps | 170 Mbps | 225 Mbps | 325 Mbps | 425 Mbps | |
| Maximum Concurrent SSL VPN Sessions | 25 | 250 | 750 | 2500 | 5000 | |
| Maximum Concurrent IPsec VPN Sessions | 25 | 250 | 750 | 2500 | 5000 | |
| Interfaces | Eight 10/100 copper Ethernet ports with dynamic port grouping. Includes two Power over Ethernet (PoE) ports, three USB ports | Five 10/100 copper Ethernet ports, two USB ports | Four 10/100/1000 copper Ethernet ports, one out-of-band management port, two USB ports | Four 10/100/1000 copper Ethernet ports, one out-of-band management port, two USB ports | Eight Gigabit Ethernet ports, four small form factor-pluggable (SFP) fiber ports, one Fast Ethernet port | |
| Profile | Desktop | 1-RU | 1-RU | 1-RU | 1-RU | |
| Stateful Failover | No | Licensed feature | Yes | Yes | Yes | |
| VPN load Balancing | No | Licensed feature | Yes | Yes | Yes | |
| Devices include a license for two SSL VPN users for evaluation and remote management purposes. The total concurrent IPsec and SSL (clientless and tunnel-based) VPN sessions may not exceed the maximum concurrent IPsec session count shown in the chart. The SSL VPN session number may also not exceed the number of licensed sessions on the device. 2Upgrade is available with Cisco ASA 5510 Security Plus license. | ||||||
| |
|









